Cyber security measures: 5 Ingenious ways Office 365 protects your data
With the GDPR (General Data Protection Regulation) deadline fast approaching businesses are working to make their data practices compliant.
And with potential fines set to reach four percent of global turnover, it’s no wonder businesses are seeking simple ways to improve their cyber security measures. To simplify compliancy management, many businesses are turning to the cloud, with more than 35 percent choosing Office 365 over its competitors. One of the key reasons for this move is Microsoft’s superior cyber protection features. Office 365 has multitude of tricks up its sleeve to keep your data safe and we’ve picked five regulatory compliance tools that will help you get up to speed.
Cyber security measure #1: Intelligent auditing and reporting
Employing a professional data officer is the ideal way to avoid hefty fines. But not every business will have the capacity to employ a full-time member of staff. With this in mind, Microsoft has recently unveiled the Compliance Manager to help you stay up to date with new data protection regulations. This service adds an additional layer of security, stopping data breaches in their tracks.
The Compliance Manager lets you audit your own business from one simple dashboard and includes user-friendly reporting tools. These allow you to easily visualise, share and tackle compliancy issues with your IT team.
Cyber security measure #2: Built-in data encryption
One of the GDPR’s key aims is to keep European citizen’s private data away from prying eyes. All companies processing the data of European citizens must reassess their cyber security measures. Even smaller businesses that deal with sensitive information, such as criminal convictions or health records are obligated to keep thorough internal data records.
This is why Office 365’s Data Encryption service is essential.
With Office 365, you can automatically encrypt emails, calendar entries and professional documents. If you do suffer a data breach only those with the encryption key can read your them. What’s more, the encryption service works on data in-transit, as well as at rest. This means files that are in the process of delivery are as secure as files uploaded to your mailbox.
Encryption technology is a popular choice for IT decision makers. The graph below shows encryption use within business areas.
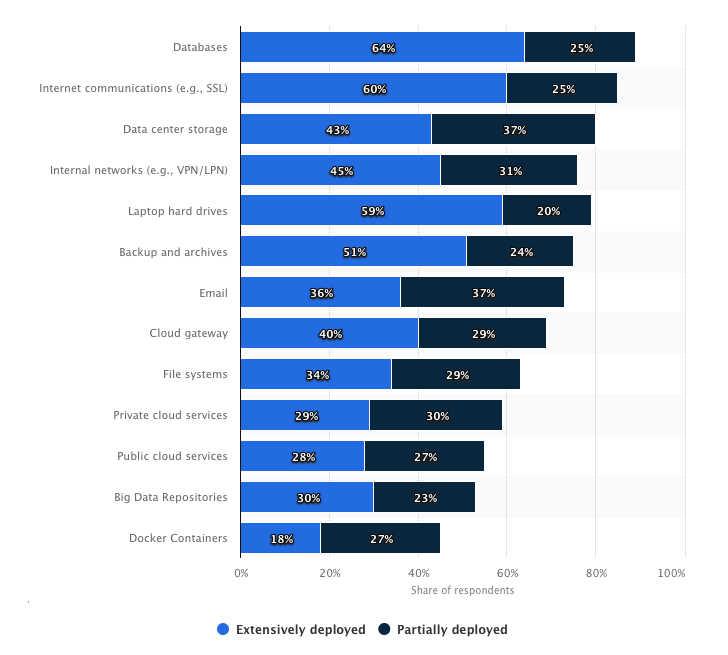
(The statistic reveals the adoption of encryption technologies across various IT business areas worldwide.)
Cyber security measure #3: Automatic data protection
Data Loss Prevention (DLP) is a godsend to any company wanting to become GDPR compliant. Using deep content analysis, DLP detects sensitive information. It then ensures it doesn’t get sent outside your company. This incredible tool integrates with SharePoint Online, OneDrive, Excel and Word.
You can either tailor what you consider to be sensitive information with the use of keywords, or use the DLP’s intuitive algorithms to accurately detect private content via:
- Internal functions
- Regular expressions
- Pattern matches
The DLP is consistently updated with the latest data regulations, helping you understand exactly what to keep under lock and key.
Cyber security measure #5: Strong passwords by default
Sometimes, it’s easy to forget the importance of the simplest security features. A lack of basic security can turn a secure, compliant business into a data breach waiting to happen.
Strong passwords are a must for any business getting GDPR compliant.
Shockingly, Leakedsource found that insecure passwords are rife on social media. Collectively, these resulted in 117 million stolen user details in 2012.
What’s more, these alarming figures suggest that these bad habits could follow your team to work.

With Office 365 strong passwords are mandatory. Each password must include:
- A unique user principal name
- 8 characters minimum
- Lowercase characters
- Uppercase characters
- Numbers
- Symbols
You can also set password expiration dates for all users. This makes hacker infiltration harder, protecting your accounts from brute force attacks.
Another key cyber security measure you can assign is App Passwords. These only give permitted devices access to Office 365 documents, allowing your team to use their own devices, without putting your data at risk.
Cyber security measure #4: Identity management
With emerging trends in Bring Your Own Device (BYOD) taking off in the modern workplace, the risk of losing your customer’s sensitive data via an employee device is enough to keep you up at night.
Mobile Device Management (MDM) is part of Office 365’s Security and Compliance Center. It allows you to monitor users’ actions on your professional portal. You can even set up alerts to detect suspicious activity on your account. These alerts are completely tailored, so you decide how stringent you want to be.
Multi-factor Authentication (MFA) is another layer of protection that you can tailor to your specific needs. This means users will have to provide another form of authentication on top of their password, including biometric fingerprint technology or a retina scan. In 2016, consumers voted biometrics as the most trustworthy authorisation method, claiming 52 percent of the vote. For more information on how to improve your firm’s password security, consider implementing multi-factor authentication.
Cyber protection is a matter of respect
More than 60 percent of IT decision makers cite PII data protection as GDPR’s greatest benefit. Yet, the public are consistently let down by the companies they trust. That’s why it’s more important than ever to invest in quality software.
By combining tailored privacy settings and reactive technology, Office 365 secures your business data, protecting customer information and making their privacy a top priority.
We’re here to help
If you want to achieve better outcomes for your business through a more intelligent use of technology, talk to us.
Contact us