Why anti-virus software is not enough to protect your business
Anti-Virus software, commonly called AV, is an critical requirement for anyone accessing the web.
AV is a software which monitors network traffic and filters out any threats that may have adverse effects on both the device and information held on it.
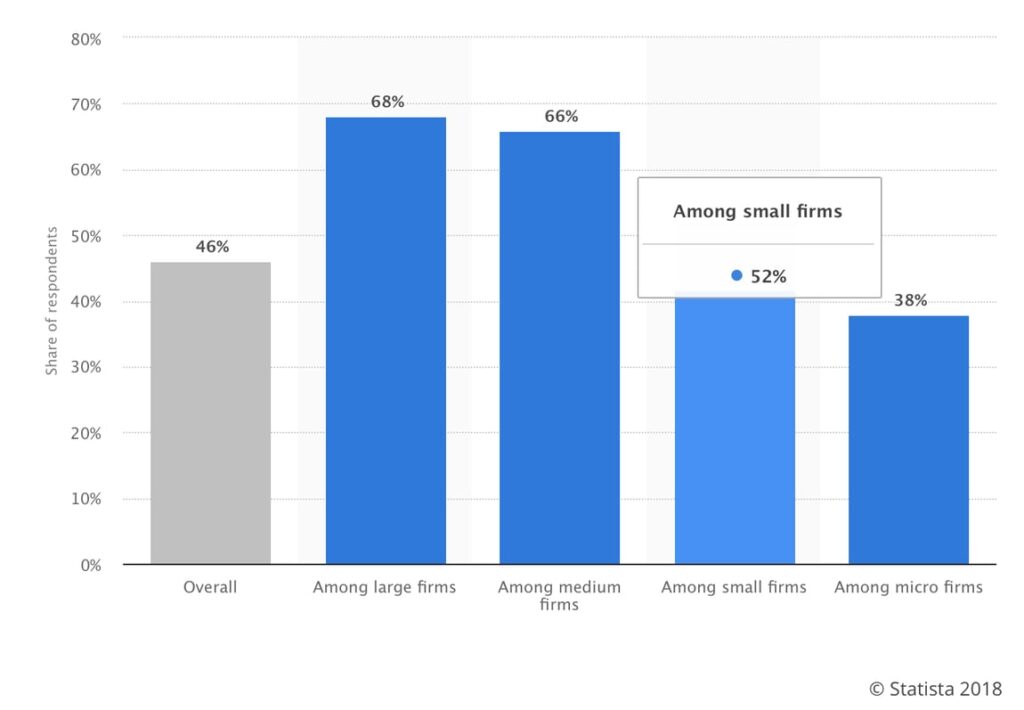
As we know, security breaches and attacks via the internet are growing and evolving constantly. In fact, 68 percent of large firms and 52 percent of small firms experienced cyber security breaches in 2017.
Stopping cyber attacks is a challenge as there are many types of viruses, and each could affect your business differently. Attackers could attempt to infiltrate your system with payload or damage viruses, malware or spyware. Often, these payloads are files or lightweight applications that run in-memory and can’t be detected as a file on the disk.
Then, if they can get inside your business, they might be trying to steal your data, monitor your people’s activity or install ransomware, which you need to pay to get removed. Other impacts of attacks are more specialised, such as constantly displaying advertisements or hijacking your IT resources for crypto-mining.
Security breaches and attacks via the internet are growing and evolving constantly. In 2023, 46% of UK businesses experienced a cyber attack, with the average cost running at £3,230. How can you protect yourself from becoming the next statistic?
In this article, we’ll show you two approaches that help you get the best cyber protection for your business.
Fighting back with AV
Various methods of tackling cybercrime have emerged. These range from constraining access to accounts, all the way up to sophisticated AV software.
It is worth to mentioning that not all AV software available will protect you as you may expect. If we look at Windows Defender as an example, an AV which is provided by Mircosoft and free to use, the software is fairly generalised, meaning it will not provide as much protection as some of the more premium softwares and will not recognise more sophisticated attacks or malwares. Therefore, Windows Defender should not be the AV software of choice for anyone working with sensitive data.

What is EDR?
Many ways to tackle cybercrime have emerged, from simply constraining access to accounts to employing sophisticated Endpoint Detection and Response (EDR) software.
EDR is software that constantly monitors end-user devices (such as computers, phones and servers) for viruses such as malware. It also records and analyses activity data, detecting anomalies in behavioural patterns which could be suspicious.
Two examples of EDR solutions are Defender for Endpoint and Defender for Business, both from Microsoft. As you would expect, they contain a long list of advanced security features that can go a long way in protecting your business, including:
- AI-powered threat detection
- Global threat intelligence that delivers a clear view of your vulnerable points
- End-to-end security for all connected devices, including Internet of Things (IoT) machines
Protecting your business
EDR is by far the best way to protect your business at this moment. Even single users who may think that it’s unlikely that they would be a direct target for attackers should consider investing in EDR. But if you’re running an organisation, you’re a much more worthwhile target for malicious users, so security should be a top priority. Therefore, EDR is a must.
How we work today means your people are exposed to more and more different cyber threats. Even if you have the best quality firewall inside your corporate network that can block many threats at the network edge, what about when people are working from home, or working on the free WiFi in Starbucks? With robust EDR on your endpoints, with web filtering and file scanning, you give yourself a much higher protection level and more chance of defeating cyber threats.
We’re in an arms race between cyber attackers and their targets (like your business). The advent of AI has given attackers new tools to play with, helping them craft evermore sophisticated ways to get past your defences. There are big bucks to be made for cyber criminals that can get past your defences. Today’s cyber attackers are highly organised and commercial, so we need to step up our game and get better at protecting ourselves. That’s why simple AV software just won’t cut it anymore. EDR is the new baseline.
What is multi-layering?
To give yourself the best level of protection (and the peace of mind that comes with it), consider multi-layering defensive security layers.
Multi-layering or layered defence refers to using a combination of different security techniques and advanced security technologies to cover a full spectrum of threat vectors. Layered defence creates multiple layers of protection across your IT systems. Elements could include:
- Endpoint protection (EDR)
- Network protection
- Data security (e.g. encryption, secure key management)
- Identity and access management – including multi-factor authentication
- Business app security
In addition, multi-layering shouldn’t be wholly technology-focused. As part of your cyber security strategy, you should include training your people on cyber awareness. You should also have robust business policies in place to minimise risk, and have a detailed cyber incident response plan. Test the effectiveness of your response plan regularly with real-time simulations.
Using multi-layering with AV software
The more scans and inspections you have in different parts of your IT systems, the better chance you have of detecting something malicious before it has the opportunity to cause serious problems.
Whether it’s AV software, your corporate firewall or Intrusion Detection and Prevention (IDPS), it all has value. These different stop points regulate all travelling data before it reaches its final destination, your internal network. Multi-layering significantly reduces the risk of attack, as any threats bypassed by the first security point can be picked up by the second or third point in your multi-layer structure.
Another benefit of multi-layering is that it increases your coverage against different threats. As we discussed earlier, there are many different types of cyber threats which can wreak different types of havoc on your business. Multi-layering allows you to take a different defensive approach to each one, if necessary.
As attackers’ methods and the nature of cyber attacks evolve, especially with the rise of new technologies like AI, taking a multi-layer approach allows you to be agile and adapt to change.
Feeling confident with multi-layering
When you combine EDR with multi-layering, you can sleep easy knowing your organisation is protected by multiple defence mechanisms.
EDR delivers that all-important understanding of what activities are happening in your IT systems. Its data analytics capabilities can spot something out of the ordinary, even if it doesn’t have a known ‘bad’ fingerprint. At the same time, a multi-layered approach gives you a better chance of spotting threats before they detonate. You’re more likely to get the precious time you need to respond to the threat.
When you invest in the right cybersecurity for your business, you can be confident you’re doing everything to protect your finances, reputation, and people. It’s just the right thing to do.

Find out more from Doherty Associates
While no software can guarantee 100% protection from cyber threats, the multi-layering and EDR approach gets you as close as possible. Don’t leave yourself open to cyber attacks that can be costly – financially and reputationally. Safeguard your business with the appropriate level of cyber protection immediately.
At Doherty Associates, we’re experts at getting organisations like yours cyber security ready. We’ll help you select cyber security software that detects threats wherever they may lie – and so much more. We’ll help you roll out the software across your organisation and be there to iron out any issues. Then, once you’re up and running, we can manage your entire cyber security strategy.
In the never-ending arms race between malicious actors and their targets, you’re better positioned to stay one step ahead with our expertise behind you.
To find out more, visit our Services page today.
We’re here to help
If you want to achieve better outcomes for your business through a more intelligent use of technology, talk to us.
Contact us