Real-World data breach examples that demand attention
Thanks to GDPR (General Data Protection Regulation), companies are more aware than ever of the issues data breaches can cause.
But what can some of the biggest data breaches in recent history teach you about your own strategy?
Unfortunately, due to the actions of some of Europe’s most trusted companies, GDPR has become an essential step in ensuring the protection of EU citizen’s data. In this blog, we take a look at four of the most famous data breach examples and examine how intelligent cloud security could prevent future disasters.
4 costly data breach examples
With the GDPR now a firm feature in business data plans, here are eight UK data breaches that helped pave the way for new EU legislation.
Data breach example #1: Wonga Loans
How many affected?
250,000 people.What happened?
Wonga, the payday loan company, was hit by a huge data breach in 2017 that compromised the bank details of 250,000 customers.How?
While a single cause is yet to be confirmed, reports point to a lack of internal security. David Emm, security researcher at Kaspersky Lab, says:
“This is yet another case of a data breach, further underlining the need for regulation. It’s to be hoped that GDPR, which comes into force in May 2018, will motivate firms to, firstly, take action to secure the customer data they hold, and secondly, to notify the ICO of breaches in a timely manner.”Is the cloud the solution?
Reports suggest that the breach was caused by Wonga not being compliant with current data protection regulations. The Compliance Manager on Microsoft’s cloud suite, Office 365, helps companies stay on top of new data regulations, manage potential risks and self-audit their compliance score against other companies.
Data breach example #2: Morrison’s supermarket
How many affected?
100,000 customers.
What happened?
Supermarket chain Morrison’s fell victim to an internal attack that lead to 100,000 employee’s personal details being leaked.How?
Employee Andrew Skelton leaked the payroll data of Morrison’s entire workforce, including bank account details and salaries. Thousands of staff have been awarded compensation payouts. The attack is reported to have cost the supermarket chain two million pounds and Skelton is serving eight years for the crime.Is the cloud the solution?
This catastrophic breach happened because Morrison’s allowed employees too much access to sensitive information. While some assume that cloud storage is less secure than on-premises, Office 365 has advanced access control features that ensure only the right eyes see sensitive documents.

Data breach example #3: Brighton and Sussex University Hospital
How many affected?
Figures are unclear, but 232 de-commissioned drives packed with patient data were stolen.What happened?
Brighton and Sussex University Hospital was fined £325,000 over the theft of thousands of patient’s data. The sensitive information, which included medical results, were reportedly put up for sale on ebay. How?
The thief accessed the sensitive data by stealing hard drives that were supposed to have been destroyed. Is the cloud the solution?
While security is often the top reason IT professionals cite for avoiding the cloud, the Brighton and Sussex Hospital breach shows just how insecure physical devices are if not invested in heavily. This disaster points to the cloud as a winning solution. By investing in a secure cloud service, companies are not obliged to destroy external devices or risk having data stolen in this manner.
Data breach example #4: LinkedIn
How many affected?
165 million accounts.What happened?
Social media platform, Linkedin, suffered a data breach that compromised the personal information of 165 million user accounts. The data has since been reported as up for sale on the dark web marketplace. How?
The data breach – which cost the company over three million pounds to clean up – has widely been reported as the result of weak user passwords and a failure on LinkedIn’s part to ‘salt’ the data.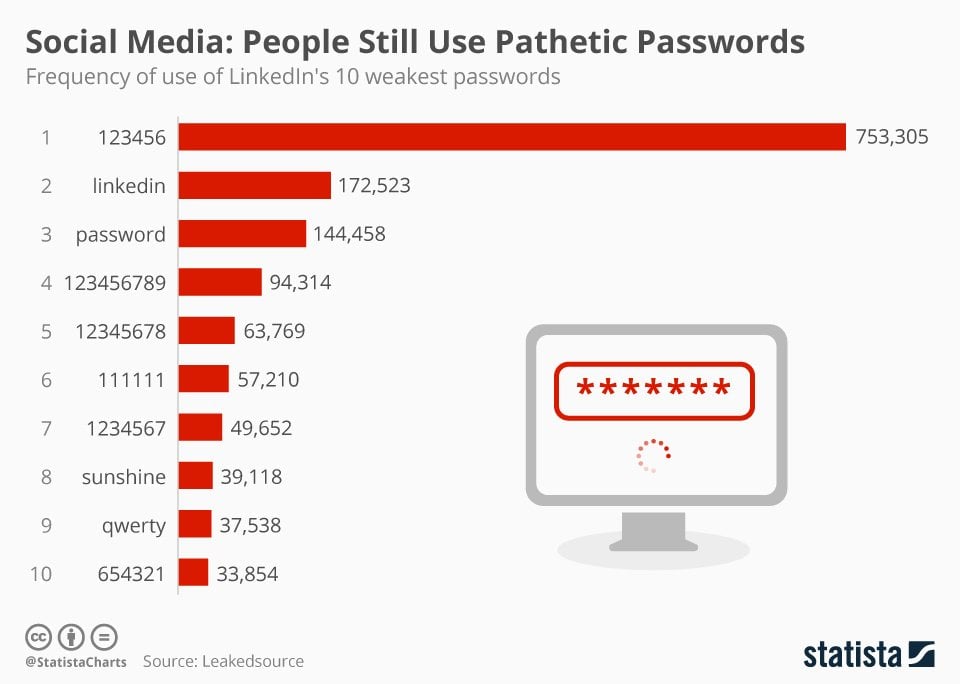
(Graph showing the most popular passwords revealed in the hack.)Is the cloud the solution?
LinkedIn’s infamous breach forces us to consider how encryption and passwords keep our data safe. The Azure cloud has a host of features that add extra security to our data via encryption and secure password management:
– Multi-factor authentication requires the use of more than one verification method, adding another layer of security.
– Azure Storage Service Encryption automatically encrypts data, making it useless to hackers.
– Key Vault, Azure’s password manager, keeps password security simple.
Data breach example #5: Vision Direct
How many affected?
It’s estimated that around 6,600 customers were affected by the breach.
What happened?
Full card numbers, expiry dates and CVV numbers were accessed in a data breach that lasted five days.
How?
A hacker stole thousands of sensitive card details in a cyber attack. It’s thought that Vision Express were storing CVV codes against regulation guidelines.
Is the cloud the solution?
Microsoft Azure continuously monitors servers, networks and applications to detect threats and ensure your infrastructure’s security is watertight. Azure’s defense protection includes:
- Intrusion detection
- Distributed denial-of-service (DDoS) attack prevention
- Penetration testing
- Behavioural analytics
- Anomaly detection
- Machine learning powered detection and testing
Staying compliant and secure is far easier when you have the right tools to monitor and mitigate advanced data threats.
Data breach example #6: Quora
How many affected?
It’s believed more than 100 million users were affected by the breach.
What happened?
The personal information of 100 million Quora users was compromised. This data potentially included:
- Sensitive account information
- User website actions
- Direct messages.
How?
An unauthorised third party gained access to one of the website’s systems, compromising millions of users’ data. As of yet, it’s still not clear how the hackers intruded the system.
Is the cloud the solution?
Hacking attempts are frequent and data breaches are becoming an inevitable part of life for businesses. However, the cloud offers security features that help to deter hackers and protect your sensitive information.
Multi-factor authentication can make it harder for cyber criminals to hack into user accounts, particularly if they require a biometric login. What’s more, automatic alerts and threat detection ensure your businesses notices any suspicious activity before it becomes a larger issue.
Data breach example #7: Dixons Carphone
How many affected?
Initially, the retailer estimated 1.2 million customer records were compromised. However, in July 2018, Dixons Carphone confirmed that the breach affected 10 million.
What happened?
Hackers accessed customer records that included sensitive information such as names, addresses and email addresses. It took the organisation a year to confirm the exact number of compromised accounts.
How?
A hacker unearthed the details of a number of payment cards, the majority of which had chip and pin protection. Although no bank details were taken, the personal records of the card holders were compromised.
Is the cloud the solution?
The main issue with Dixon Carphone’s enormous real-world data breach is, of course, the delay in recognising the extent of the damage. The main culprit of this delay was poor system visibility and inadequate threat detection.
Using the power of the cloud, businesses can gain a better insight into suspicious behaviours, track unusual patterns, and take action before the problem escalates.
Data breach example #8: Sage
How many were affected?
Between 200-300 of Sage’s customers.
What happened?
Customer data was compromised, causing reputational damage to the organisation. Shares in Sage fell by as much as 4.3 percent after the incident occurred.
How?
An employee of the firm gained unauthorised access to the employee data of hundreds of UK firms by using an internal login.
Is the cloud the solution?
Although you can never anticipate the motivations of any one person, the cloud enables you to control which employees access highly sensitive information. By using Azure Active Directory’s identity management and restricting the number of employees who can see or handle crucial data, you’ll limit the chance of becoming yet another real world data breach example.
Safety first: how to avoid a security breach
Worried about privacy and compliancy issues in your business? Avoid any nasty surprises by building your storage infrastructure on solid foundations.
The cloud is making the world of a data a much safer place. With advanced security features, reactive software and privacy by design, data breaches will soon be easier to deal with and less of a threat to your business reputation.
If you’re unsure if your company’s data strategy is up to scratch check, book a meeting with one of our certified professionals. Don’t risk becoming victim to an avoidable breach – get GDPR compliant today.
Editor’s note: This post was originally published in April 2018 and has since been updated and revamped with new, relevant content. Enjoy!
Written by: Doherty
We’re here to help
If you want to achieve better outcomes for your business through a more intelligent use of technology, talk to us.
Contact us